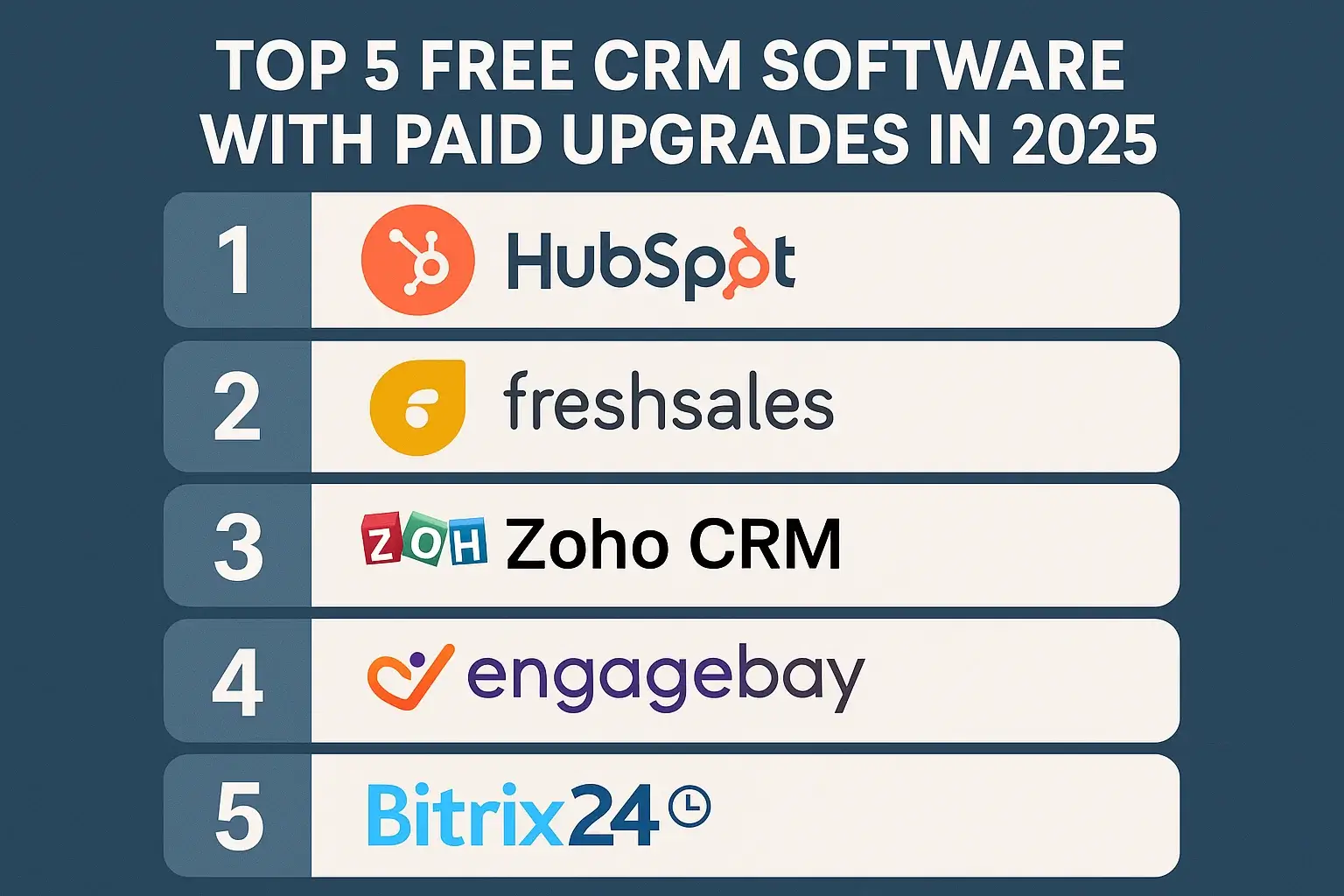
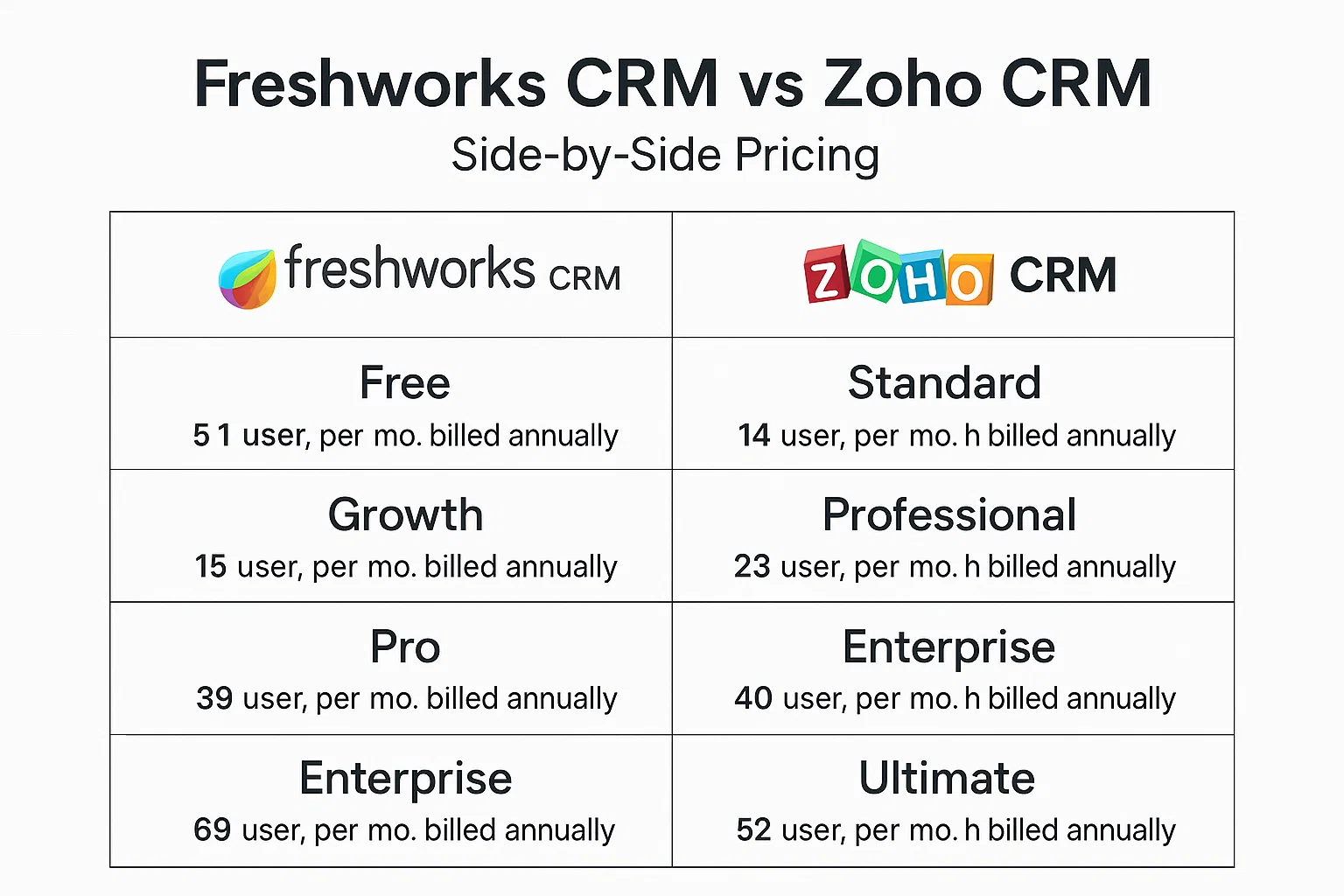
Introduction to Cloud CRM Security
Cloud CRM solutions have become ubiquitous in modern business, offering flexibility, scalability, and real-time access to customer data. However, with this migration to the cloud comes significant concerns about data security, privacy, and compliance. In 2025, understanding how secure cloud CRM systems are is essential for businesses to protect their sensitive customer information.
Core Security Features of Cloud CRM Platforms
- Data Encryption: Industry-standard AES-256 encryption for data at rest and in transit ensures that CRM data is unreadable by unauthorized users.
- Multi-Factor Authentication (MFA): Adds a critical layer of security to user logins, significantly reducing the risk of unauthorized access.
- Role-Based Access Control (RBAC): Limits data access based on user roles, ensuring employees see only what they need.
- Automated Security Updates: Cloud CRM providers deploy frequent patches and updates to mitigate emerging vulnerabilities.
- Compliance Certifications: Leading cloud CRMs maintain compliance with GDPR, HIPAA, CCPA, and industry-specific regulations.
- Backup and Disaster Recovery: Automated daily backups and tested recovery plans protect against data loss.
Emerging AI-Driven Security Measures
AI-powered security solutions are transforming cloud CRM protection by providing intelligent threat detection and automated responses. Key AI features include anomaly detection, behavioral analytics, and predictive risk assessment, which help organizations stay ahead of cyber threats.
| Security Feature | Description | Business Benefit |
|---|---|---|
| Encryption | Ensures data privacy through AES-256 standards for data in transit and at rest | Protects against data breaches and unauthorized data access |
| Multi-Factor Authentication | Requires additional verification for user login | Reduces risk of credential theft and account compromise |
| AI Threat Detection | Uses machine learning to identify unusual access or data use patterns | Enables proactive threat mitigation and faster incident response |
| Role-Based Access Control | Restricts data access based on job function | Limits damage from insider threats and accidental data exposure |
| Automated Backups | Regular data snapshots stored securely offsite | Ensures data recovery after accidental deletion or attacks |
Common Security Risks for Cloud CRM
- Phishing and social engineering attacks targeting CRM credentials
- Data breaches due to misconfiguration or weak access controls
- Unauthorized third-party integrations without sufficient security evaluation
- Insider threats from both malicious and careless employees
- Outdated software lacking critical security patches
Best Practices for Securing Cloud CRM Data
- Implement multi-factor authentication for all users
- Regularly audit user roles and permissions
- Monitor access logs and enable anomaly detection alerts
- Ensure encryption is active on all data storage and transmission
- Keep CRM software up-to-date with latest security patches
- Establish a disaster recovery plan including regular data backups
- Train employees on security awareness and phishing prevention
Conclusion
Cloud CRM systems in 2025 are designed with robust security features and benefit from AI-driven protection, making them highly secure when appropriately managed. Businesses must adopt best practices and leverage these technologies to protect sensitive data, maintain compliance, and build trust with their customers.
 Admin
Admin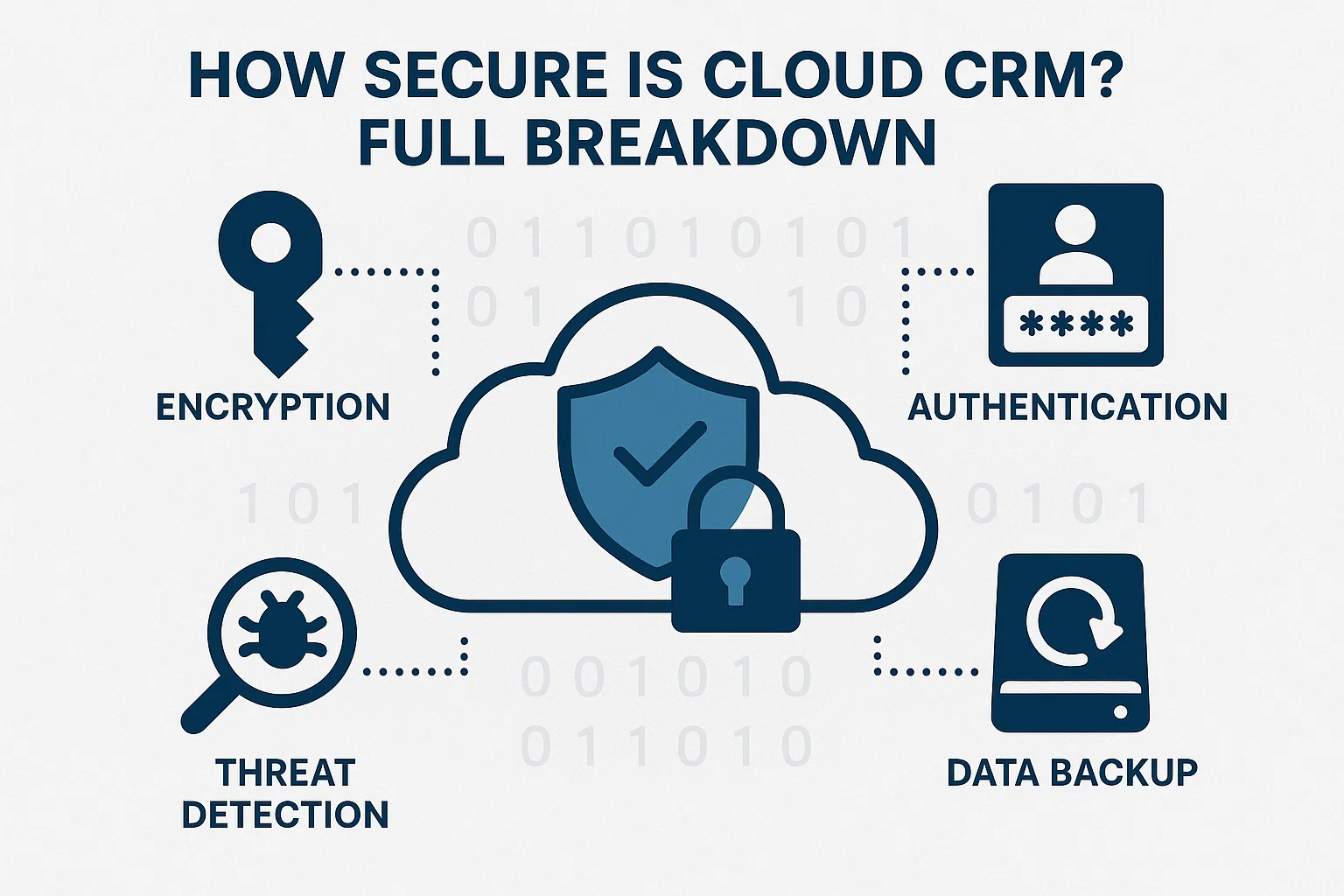

 Admin
Admin